Day Two of Pwn2Own Automotive 2026 was packed with action, and the stakes continued to rise. Security researchers returned to the Pwn2Own stage, probing and challenging the latest automotive systems as the competition intensified. New exploits, unexpected twists, and standout performances emerged throughout the day - follow along here for daily updates as the race for Master of Pwn heats up.
Following an action-packed Day One, where $516,500 USD was awarded for 37 unique 0-day vulnerabilities, Day Two added another $439,250 USD and 29 unique 0-days, bringing the event totals to $955,750 USD with 66 unique vulnerabilities overall. Fuzzware.io holds a commanding lead for Master of Pwn, but with one day to go, anything can still happen. We’ll see what the final day of the contest brings.
SUCCESS - Inhyung Lee, Seokhun Lee, Chulhan Park, Wooseok Kim, and Yeonseok Jang of Team MAMMOTH exploited a command injection vulnerability against the Alpine iLX-F511, earning $10,000 USD and 2 Master of Pwn points.
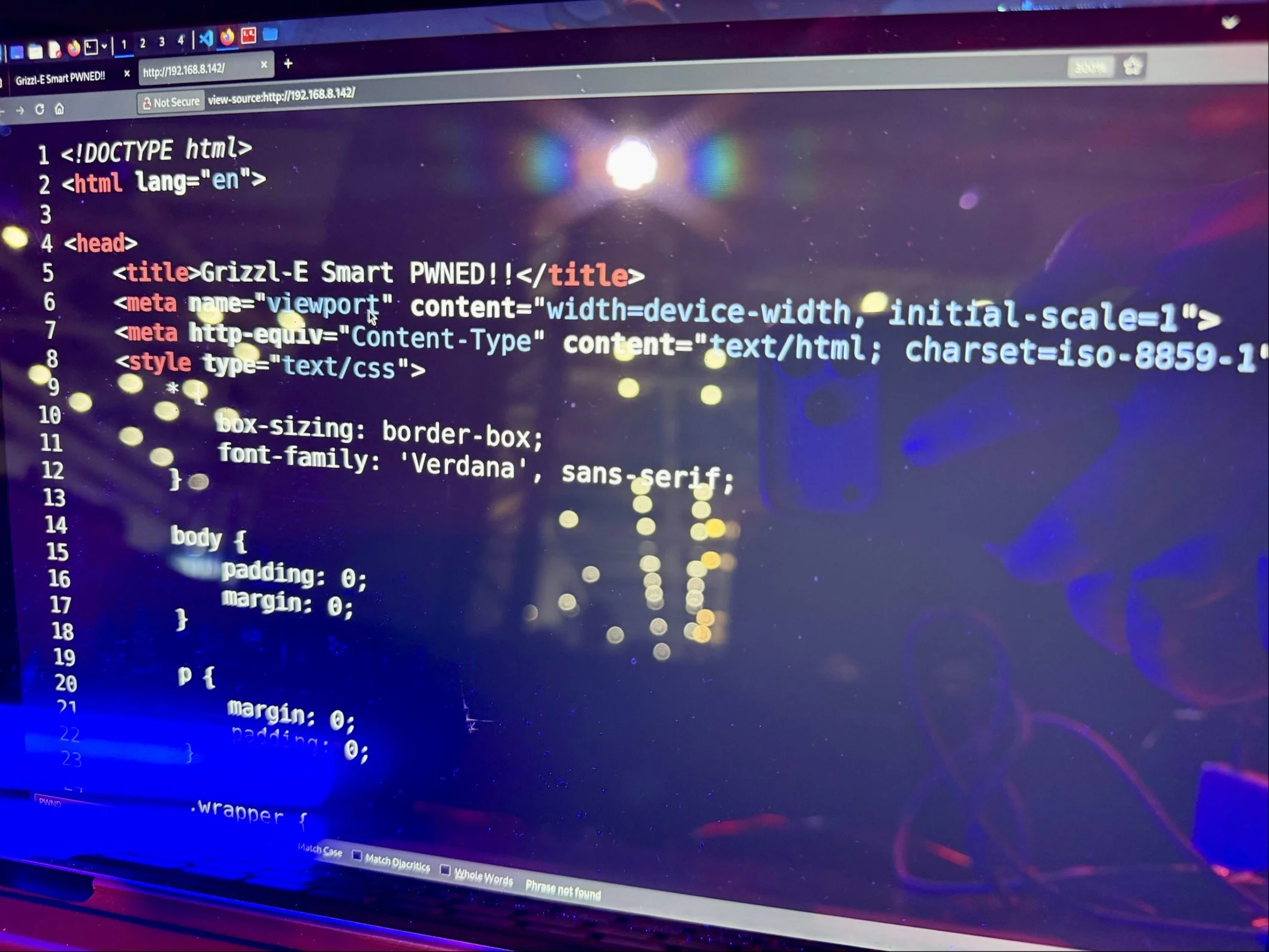
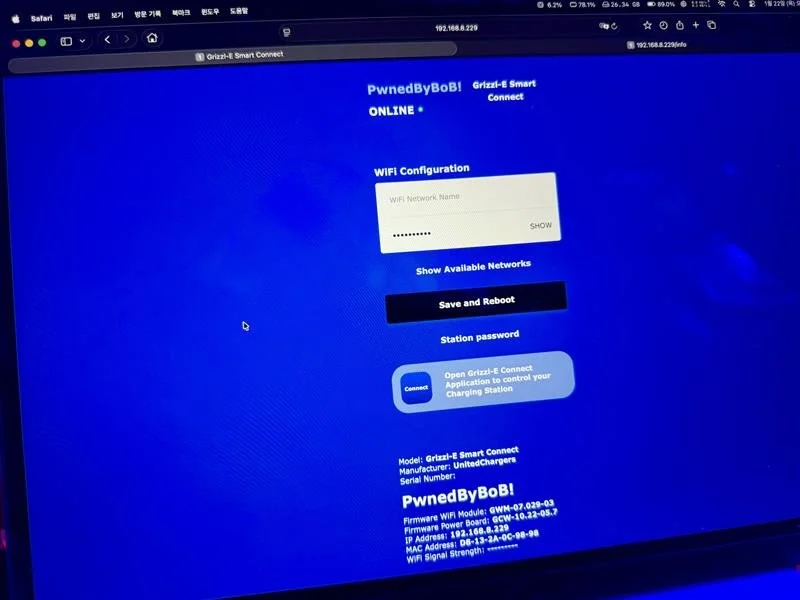
FAILURE - Autocrypt - Hoyong Jin, Jaewoo Jeong, Chanhyeok Jung, Minsoo Son, and Kisang Choi - targeted the Grizzl‑E Smart 40A with the Charging Connector Protocol/Signal Manipulation add‑on but were unable to demonstrate the vulnerability within the allotted time.
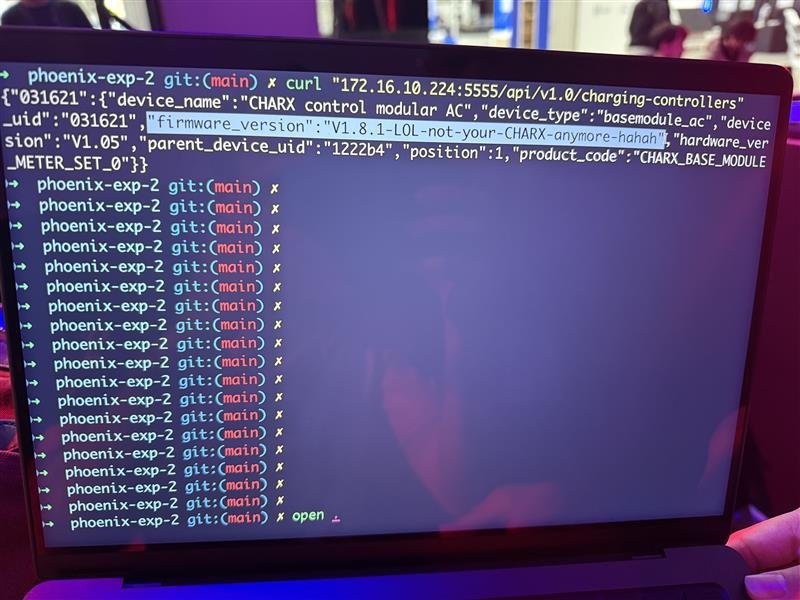
SUCCESS - Julien COHEN‑SCALI of FuzzingLabs (@FuzzingLabs) targeted the Phoenix Contact CHARX SEC‑3150, chaining two vulnerabilities - an authentication bypass and privilege escalation - to earn $20,000 USD and 4 Master of Pwn points.
SUCCESS - Neodyme AG (@Neodyme) exploited a buffer overflow vulnerability (CWE‑120) in Round 3 to achieve privileged code execution on the Sony XAV‑9500ES, earning $10,000 USD and 2 Master of Pwn points. #Pwn2Own #P2OAuto
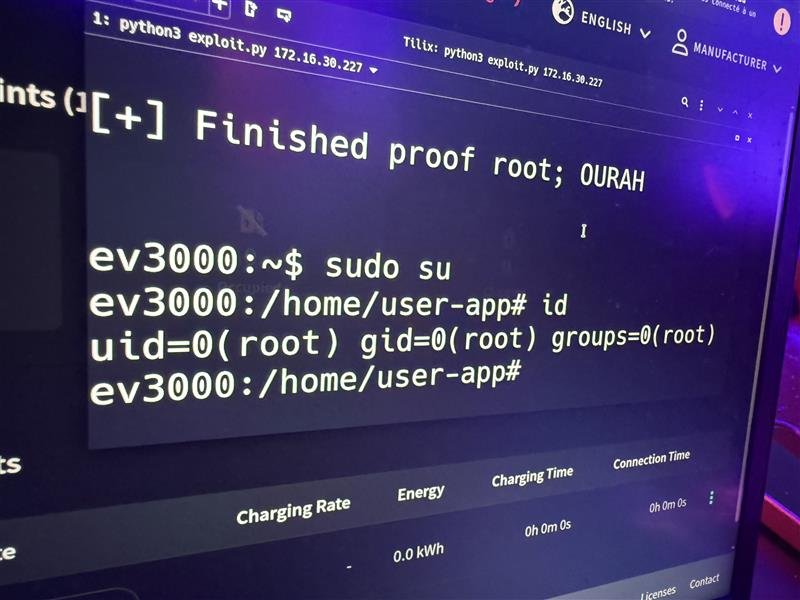
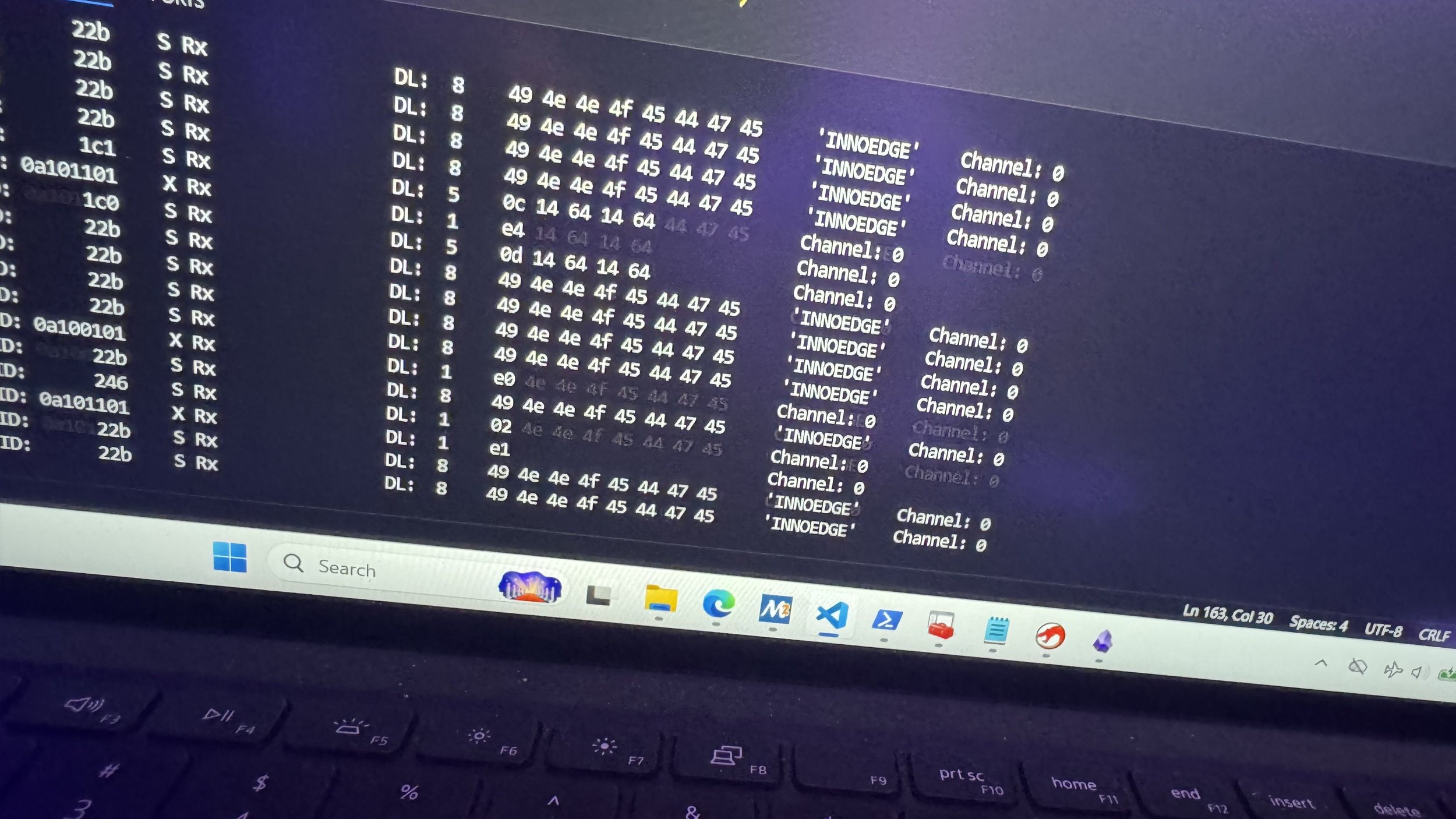
SUCCESS - Hank Chen (@hank0438) of InnoEdge Labs exploited an exposed dangerous method against the Alpitronic HYC50 – Lab Mode, earning $40,000 USD and 4 Master of Pwn points.
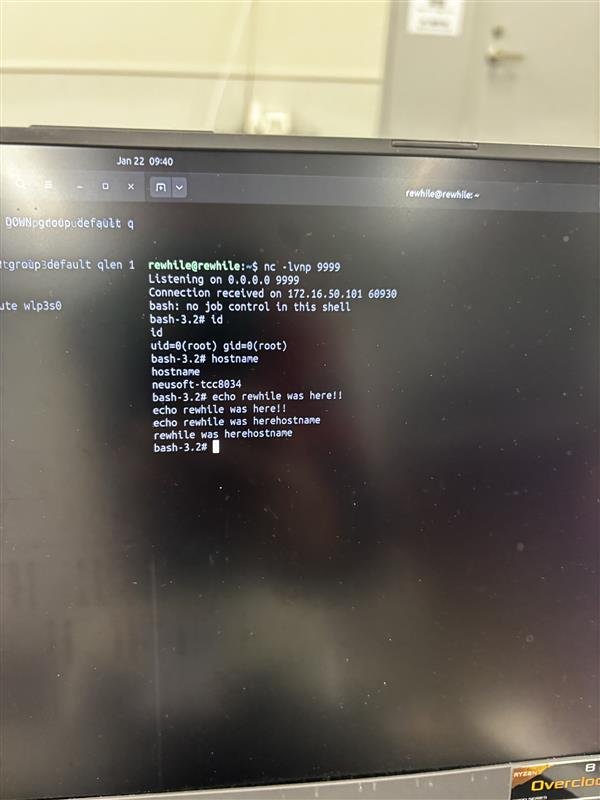
SUCCESS / COLLISON - Nguyen Thanh Dat (@rewhiles) of Viettel Cyber Security (@vcslab) targeted the Alpine iLX-F511, hitting a one-vulnerability collision with a previous attempt and earning $2,500 USD and 1 Master of Pwn point.
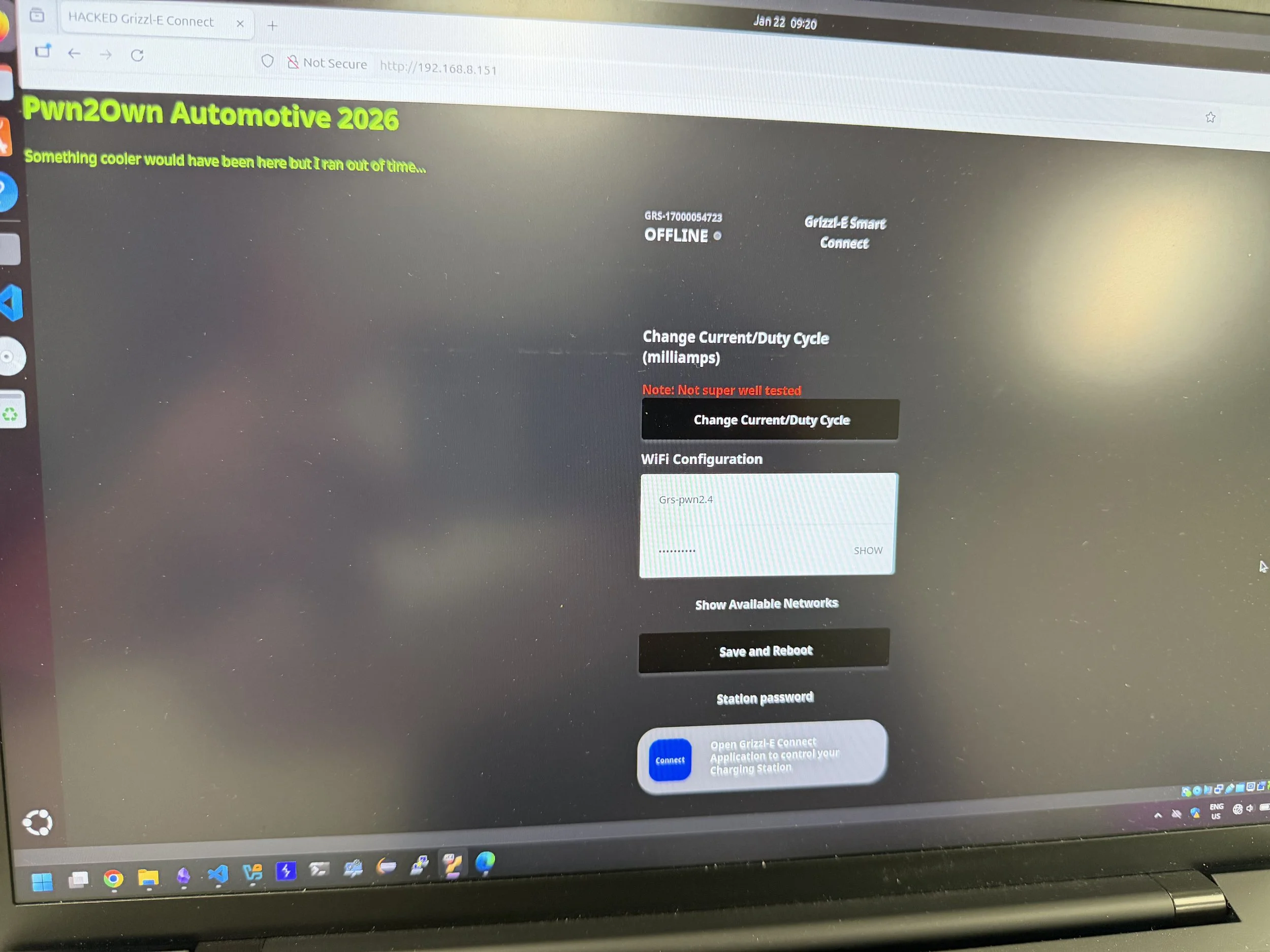
SUCCESS / COLLISON - BoredPentester (@BoredPentester) targeted the Grizzl‑E Smart 40A with the Charging Connector Protocol/Signal Manipulation add‑on, combining two bugs to earn $20,000 USD and 3 Master of Pwn points. #Pwn2Own #P2OAuto
SUCCESS / COLLISON - Bongeun Koo (@kiddo_pwn) and Evangelos Daravigkas (@freddo_1337) of Team DDOS targeted the Kenwood DNR1007XR, exploiting an n‑day command injection to earn $4,000 USD and 1 Master of Pwn point.
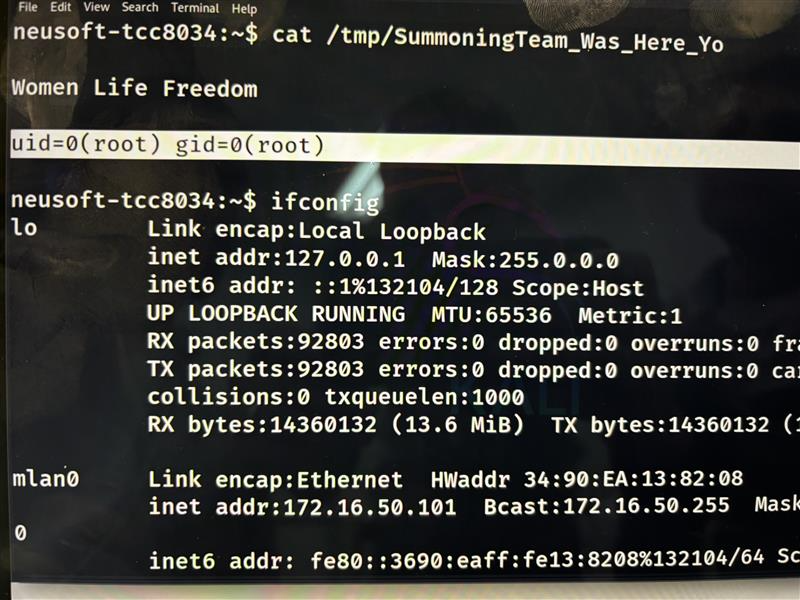
SUCCESS - Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) targeted the Kenwood DNR1007XR in Round 6, exploiting a command injection vulnerability to earn $5,000 USD and 2 Master of Pwn points.
SUCCESS / COLLISON - Kazuki Furukawa (@N4NU) of GMO Cybersecurity by Ierae targeted the Alpine iLX-F511, hitting a one-vulnerability collision with a previous attempt and earning $2,500 USD and 1 Master of Pwn point. #Pwn2Own #P2OAuto
SUCCESS / COLLISON - Donggeon Kim (@gbdngb12), Hoon Nam (@pwnstar96), Jaeho Jeong (@jeongZero), Sangsoo Jeong (@sangs00Jeong), and Wonyoung Jung (@nonetype_pwn) of 78ResearchLab targeted the Kenwood DNR1007XR, exploiting one n-day vulnerability along with two collisions to earn $2,500 USD and 1 Master of Pwn point.
SUCCESS - Xilokar (xilokar@mamot.fr) targeted the Alpitronic HYC50 – Lab Mode, exploiting one bug to earn $20,000 USD and 4 Master of Pwn points.
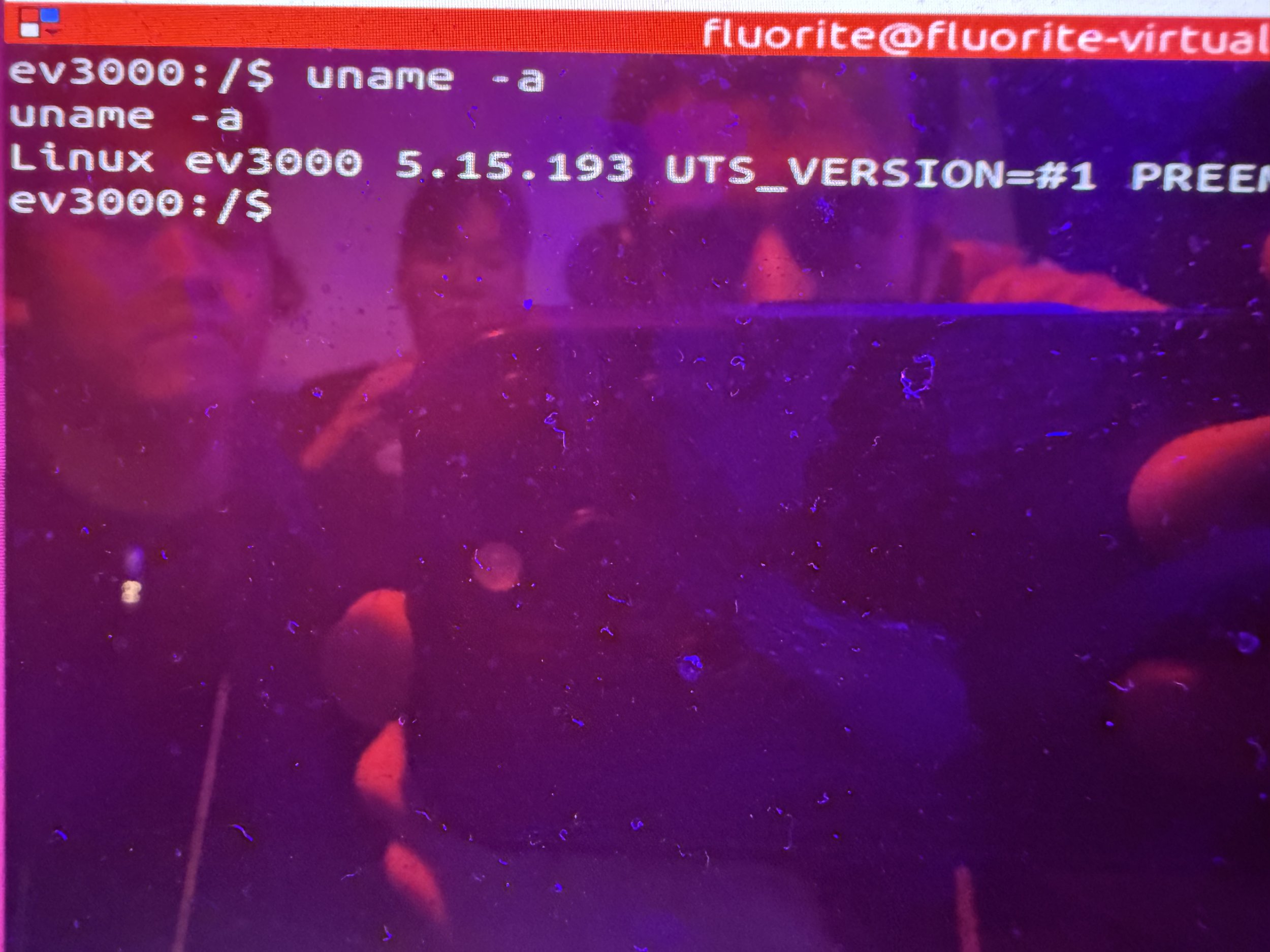
SUCCESS / COLLISON - Hyeongseok Lee (@fluorite_pwn), Yunje Shin (@YunjeShin), Chaeeul Hyun (@yskm_Gunter), Ingyu Yang (@Mafty5275), Hoseok Kang (@cl4y419), Seungyeon Park (@vvsy46), and Wonjun Choi (@won6_choi) of BoB::Takedown targeted the Grizzl-E Smart 40A, hitting one collision and one unique 0-day, earning $15,000 USD and 3 Master of Pwn points.
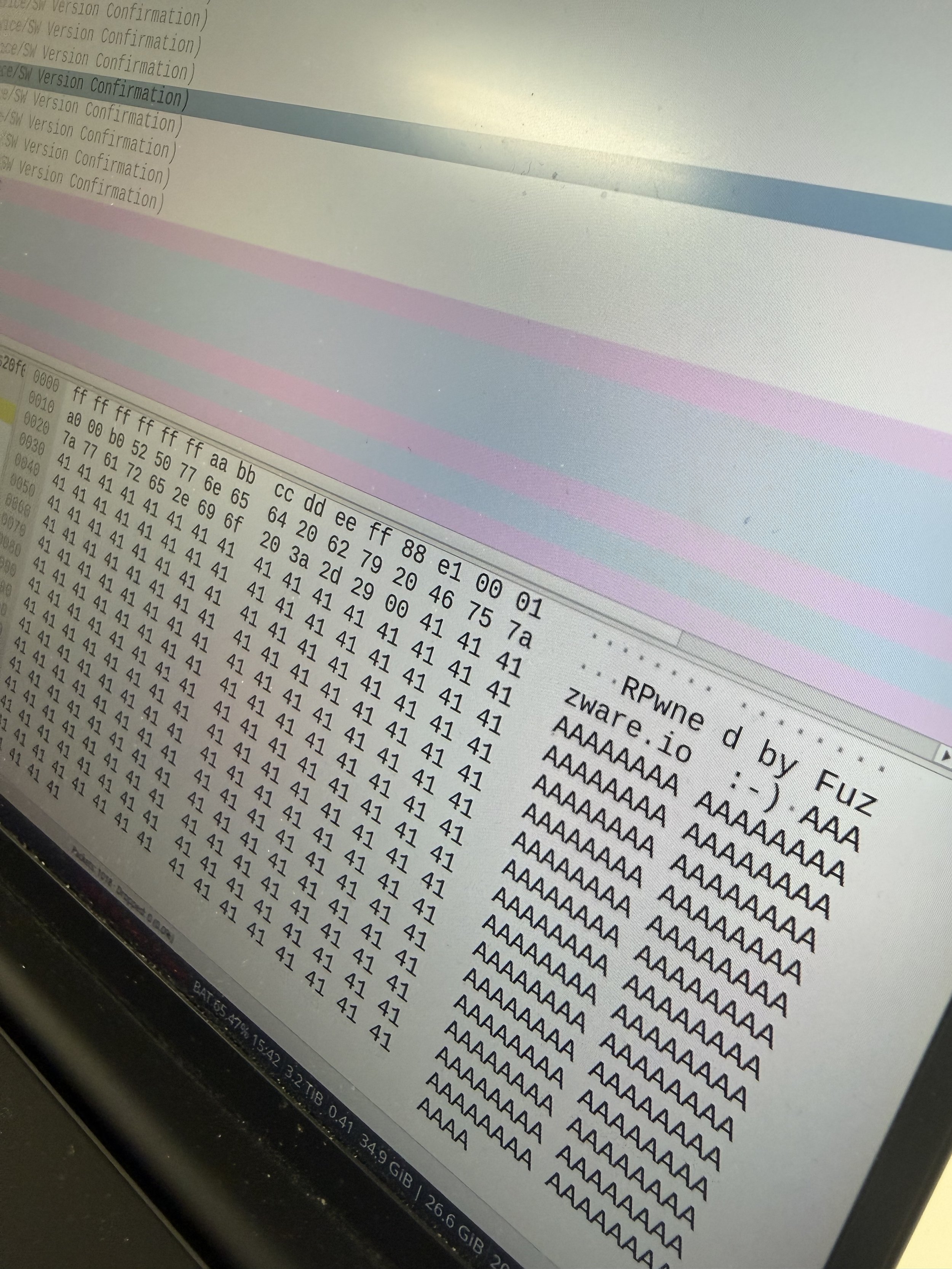
SUCCESS - Tobias Scharnowski (@ScepticCtf), Felix Buchmann (@diff_fusion), and Kristian Covic (@SeTcbPrivilege) of Fuzzware.io targeted the Phoenix Contact CHARX SEC-3150 in Round 5, exploiting three bugs with two add-ons to earn $50,000 USD and 7 Master of Pwn points.
SUCCESS / COLLISON - Slow Horses of Qrious Secure (@qriousec) targeted the Alpine iLX-F511, resulting in a single vulnerability collision with a previous attempt, earning $2,500 USD and 1 Master of Pwn point.
FAILURE - Autocrypt (Hoyong Jin, Jaewoo Jeong, Chanhyeok Jung, Minsoo Son, and Kisang Choi) targeted the Autel MaxiCharger AC Elite Home 40A with the Charging Connector Protocol/Signal Manipulation add-on, but ran out of attempts before the exploit could be demonstrated.
SUCCESS - BoredPentester (@BoredPentester) targeted the Kenwood DNR1007XR, demonstrating a command injection vulnerability to earn $5,000 USD and 2 Master of Pwn points.
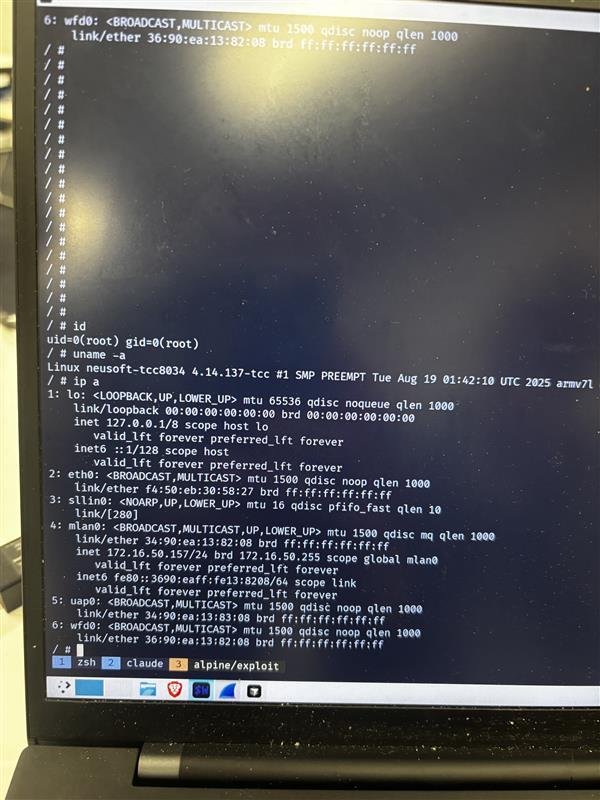
SUCCESS - Rob Blakely of Technical Debt Collectors targeted Automotive Grade Linux, chaining three bugs - an out-of-bounds read, memory exhaustion, and a heap overflow - to earn $40,000 USD and 4 Master of Pwnpoints. #Pwn2Own #P2OAuto
SUCCESS / COLLISON - PHP Hooligans / Midnight Blue (@midnightbluelab) targeted the Autel MaxiCharger AC Elite Home 40A with the Charging Connector Protocol/Signal Manipulation add-on, hitting a full collision on a two-bug chain, earning $20,000 USD and 3 Master of Pwn points. #Pwn2Own #P2OAuto
SUCCESS - Synacktiv (@synacktiv) targeted the Autel MaxiCharger AC Elite Home 40A with the Charging Connector Protocol/Signal Manipulation add‑on. In Round 2, they exploited one stack‑based buffer overflow, earning $30,000 USD and 5 Master of Pwn points.
SUCCESS - Tobias Scharnowski (@ScepticCtf), Felix Buchmann (@diff_fusion), and Kristian Covic (@SeTcbPrivilege) of Fuzzware.io targeted the ChargePoint Home Flex (CPH50-K) with the Charging Connector Protocol/Signal Manipulation add-on, exploiting one command injection bug to earn $30,000 USD and 5 Master of Pwn points. #Pwn2Own #P2OAuto
FAILURE - PetoWorks (@petoworks) targeted the Alpine iLX-F511 but was unable to demonstrate their exploit within the allotted time.
SUCCESS - Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) targeted the ChargePoint Home Flex (CPH50-K) with the Charging Connector Protocol/Signal Manipulation add-on, exploiting two bugs to earn $30,000 USD and 5 Master of Pwn points.
SUCCESS / COLLISON - PetoWorks (@petoworks) targeted the Kenwood DNR1007XR, hitting one bug collision earning $2,500 USD and 1 Master of Pwn point.
SUCCESS / COLLISON - Tobias Scharnowski (@ScepticCtf), Felix Buchmann (@diff_fusion), and Kristian Covic (@SeTcbPrivilege) of Fuzzware.io targeted the Grizzl-E Smart 40A with the Charging Connector Protocol/Signal Manipulation add-on, resulting in two bug collisions and earning $15,000 USD and 3 Master of Pwn points.
SUCCESS / COLLISON - Bongeun Koo (@kiddo_pwn) and Evangelos Daravigkas (@freddo_1337) of Team DDOS targeted the Phoenix Contact CHARX SEC-3150 with the Charging Connector Protocol/Signal Manipulation add-on, demonstrating six bugs but encountering a collision, still earning $19,250 USD and 4.75 Master of Pwn points.
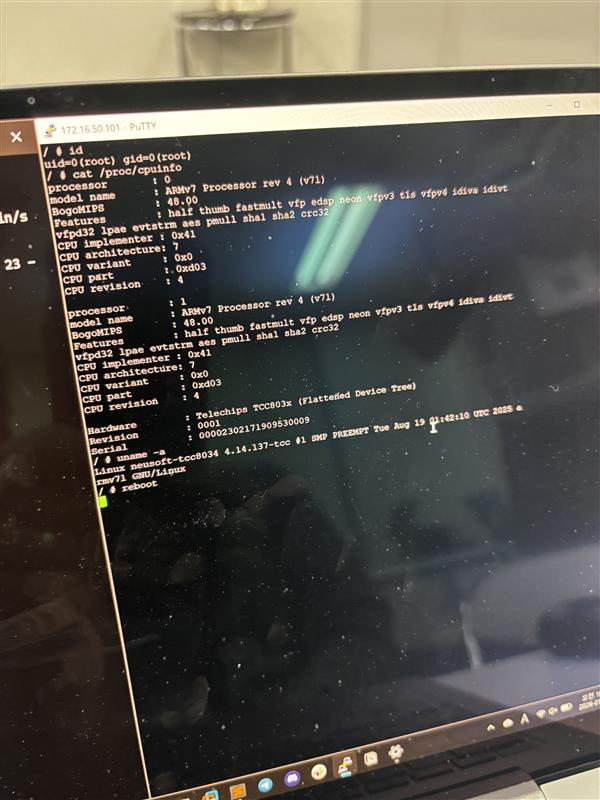
SUCCESS - Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) targeted the Alpine iLX-F511, exploiting two unique vulnerabilities to gain root access, earning $5,000 USD and 2 Master of Pwn points.
SUCCESS / COLLISON - Evan Grant (@stargravy) targeted the Grizzl-E Smart 40A with the Charging Connector Protocol/Signal Manipulation add-on, hitting two bug collisions, still earning $15,000 USD and 3 Master of Pwn points.
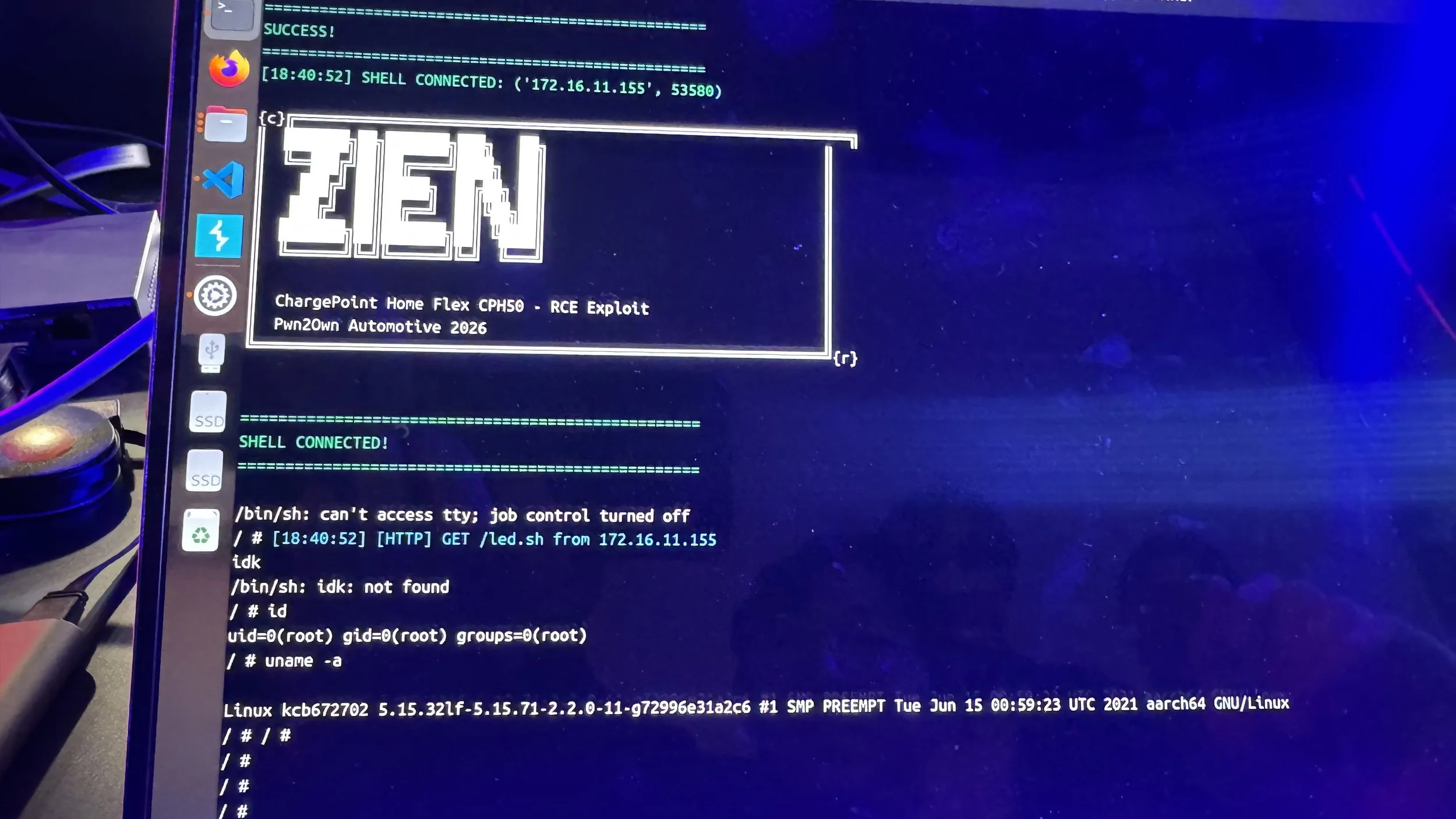
SUCCESS / COLLISON - Hyeonjun Lee (@gul9ul), Younghun Kwon (@d0kk2bi), Hyeokjong Yun (@dig06161), Dohwan Kim (@neko__hat), Hanryeol Park (@hanR0724), Hyojin Lee (@meixploit), Jinyeong Yoon, and Youngmin Cho (@ZIEN0621) of ZIEN, Inc. targeted the ChargePoint Home Flex (CPH50-K), demonstrating two unique bugs (symlink following and command injection) but encountered a collision with a previous attempt - still earning $16,750 USD and 3.5 Master of Pwn points.
SUCCESS / COLLISON - Hyeongseok Lee (@fluorite_pwn), Yunje Shin (@YunjeShin), Chaeeul Hyun (@yskm_Gunter), Ingyu Yang (@Mafty5275), Hoseok Kang (@cl4y419), Seungyeon Park (@vvsy46), and Wonjun Choi (@won6_choi) of BoB::Takedown targeted the Phoenix Contact CHARX SEC-3150, demonstrating three bugs, but ran into two collisions, earning $6,750 USD and 2.75 Master of Pwn points.